One Identity (OI)
One Identity is a Quest software company that helps organizations to successfully implement professional identity and access management. Its comprehensive product range and holistic approach enables companies to realize their individual IT security strategy locally, in the cloud or in a hybrid environment.
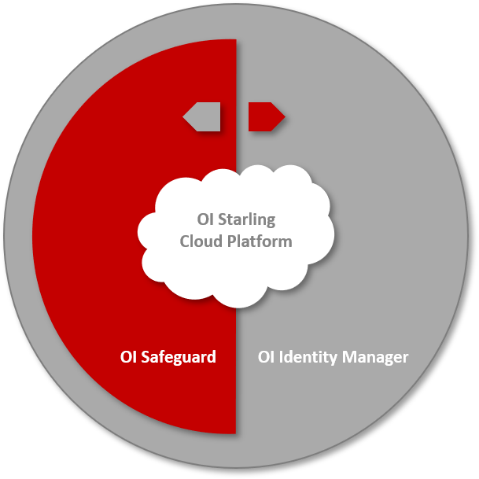
Step by step to holistic IT security
In times of digital transformation, it is more important than ever to minimize the opportunity for internal and external threats. One Identity has developed numerous software modules for this purpose, which complement each other and can be combined with each other for increased security. Thus, the One Identity product range supports companies in implementing a holistic identity-based IT security strategy step by step.
SailPoint
SailPoint is the worldwide market leader for identity security in the modern enterprise. With the SailPoint Identity Security Cloud (ISC), the company provides a unified, AI-driven SaaS platform. It enables organizations to centrally manage access to applications and data, offering complete visibility across all identities – whether human workforce, third-party, or machine identities.
Intelligent automation for complex requirements
The technology relies on autonomous identity governance to proactively minimize security risks. By leveraging artificial intelligence and machine learning, SailPoint ISC automates complex administrative processes, from certification to provisioning. This ensures adherence to strict compliance standards and operatively relieves IT teams by replacing static policies with dynamic, risk-based access controls.
More about SailPoint
SAP
SAP offers both cross-industry and industry-specific solutions in the fields of GRC and identity management. Technical solutions for the separation of functions and monitoring are included in the SAP Compliant Identity Management Suite. SAP Access Control is one of the three pillars of this product group, along with SAP Identity Management and SAP Single Sign-On..
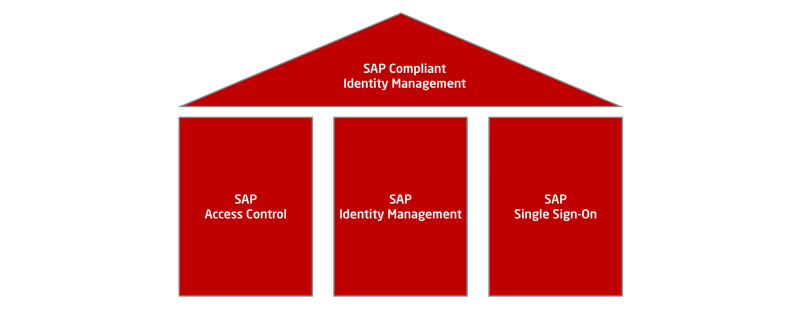
50 years of experience in enterprise software
As one of the world's largest providers of enterprise applications, SAP also offers comprehensive IT security solutions for all business areas. They help to meet current and future security requirements in your company efficiently and sustainably. You too can benefit from 50 years of development experience in the field of IT security software.
Microsoft Entra ID
Microsoft Entra is a platform from Microsoft that provides a variety of identity and access management solutions to protect identities and securely access apps and resources across multi-cloud environments. Microsoft Entra ID is the solution recommended by SAP after the SAP IdM end of maintenance for identity management in companies.
Microsoft currently offers 6 products with the Entra ID Suite for corporate identities. ASCONSIT's initial focus is on Entra ID governance.

Another alternative SAP IdM migration solution
With the end of SAP IdM maintenance, Microsoft Entra ID is the successor recommendation for SAP IdM called by SAP. Microsoft Entra ID is a cloud-based solution for managing identities and access in the company. In particular, from a procedural point of view, ASCONSIT offers a classification under the aspects of on-prem necessities and their resulting limits of a pure IAM cloud solution, as well as the classification in the context of the special governance requirements from the customer's point of view.









